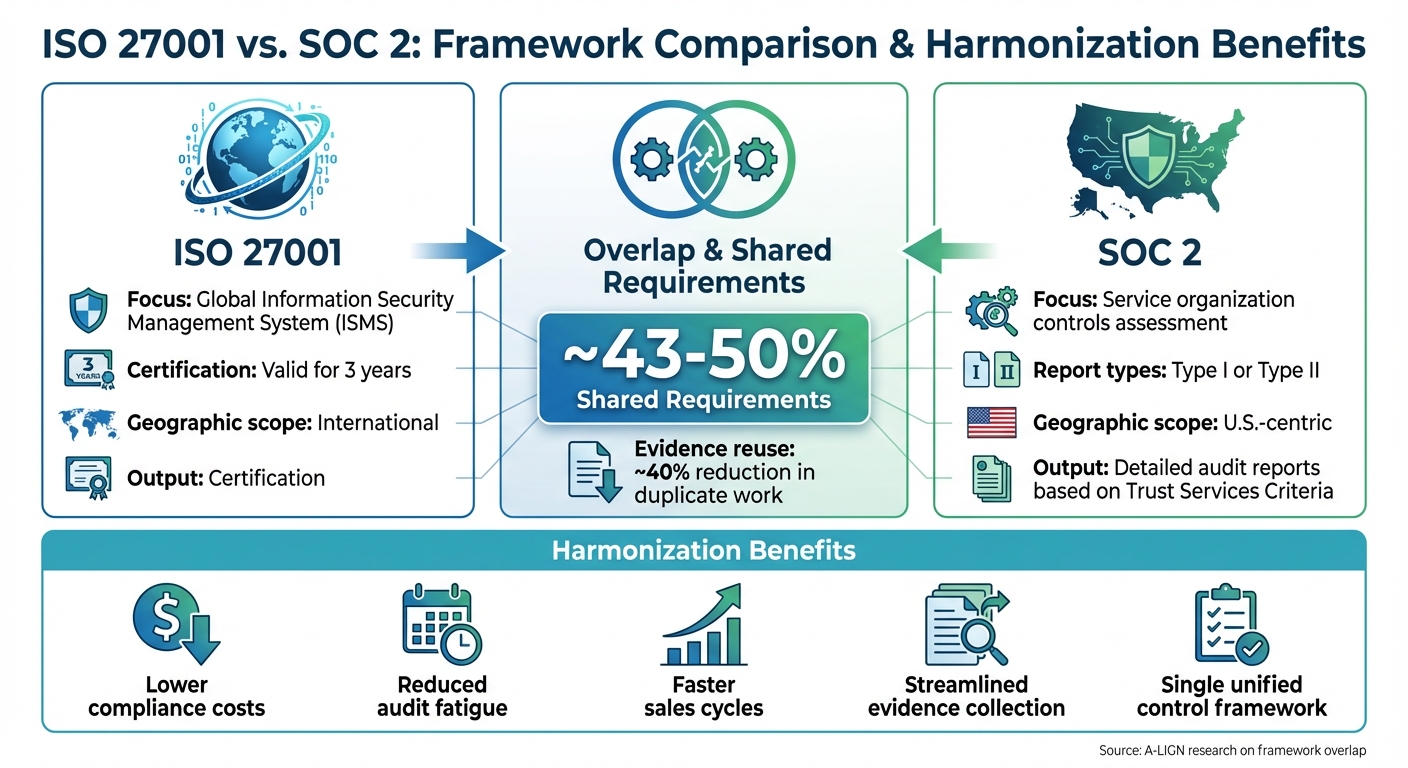
Combining ISO 27001 and SOC 2 saves time, reduces costs, and simplifies compliance. These two frameworks share nearly half of their requirements, making it possible to streamline your efforts by aligning policies, controls, and audits. Here's what you need to know:
- ISO 27001 focuses on building a global Information Security Management System (ISMS) with certification valid for three years.
- SOC 2 assesses a U.S.-centric service organization's controls, offering detailed reports (Type I or II) based on Trust Services Criteria.
- Harmonizing these frameworks allows businesses to meet both U.S. and global security requirements efficiently.
ISO 27001 vs SOC 2: Framework Comparison and Harmonization Benefits
Core Areas for Alignment Between ISO 27001 and SOC 2
Scope, Context, and Stakeholder Alignment
Start by drafting a unified scope statement that works for both ISO 27001 and SOC 2. This document should clearly outline the systems, locations, and services included in the scope. For example, it might describe a cloud-based SaaS platform hosted on AWS that serves both domestic and international clients. To avoid discrepancies during audits, use the stricter scoping requirements as your baseline.
Next, identify the key stakeholders involved. These typically include executive leadership, IT and security teams, DevOps, HR, Legal, Sales, major customers, and critical vendors. Gather their specific requirements for each framework. For instance, some customers may require SOC 2 Type II compliance, while others might demand ISO 27001 certification. Additionally, review contractual and regulatory requirements - such as HIPAA, GLBA, or state privacy laws - and map them to ISO 27001 controls and SOC 2 Trust Services Criteria. This allows you to address multiple obligations with a single set of controls.
To streamline communication and minimize conflicting expectations, conduct joint workshops with stakeholders. Use these sessions to review the unified scope, shared policies, and the organization’s risk appetite. This collaborative approach ensures everyone is aligned and prepared when working with auditors.
Once the scope and stakeholder alignment are in place, the next step is to synchronize risk management practices.
Unified Risk Management and Control Objectives
Develop a risk assessment process that meets the requirements of ISO 27001 Clause 6 and aligns with SOC 2 common criteria like CC3 and CC9. Define a methodology that includes clear criteria for evaluating likelihood and impact (both quantitatively, such as financial loss, and qualitatively). Perform these assessments at least once a year or whenever major changes occur. This helps identify threats, vulnerabilities, assets, and existing controls.
Maintain a single, unified risk register. This should document assets, threats, vulnerabilities, risks, and the assigned owners, along with treatment options and control mappings (e.g., CC3.2, A.8.2). Keep the register updated through quarterly reviews, incorporating insights from vulnerability scans, incident analyses, and vendor assessments. Present this consolidated risk register during audits as evidence of your centralized approach to risk management. This not only simplifies audit preparation but also reduces redundant efforts.
After establishing a unified approach to risk management, focus on standardizing controls across both frameworks.
Integrated Control Framework and Mapping
Build a control catalog that serves as a centralized reference for both ISO 27001 and SOC 2. Each entry should include the control’s ID, description, owner, implementation frequency, evidence type, and current status. Add mapping fields to connect ISO 27001 Annex A controls with SOC 2 Trust Services Criteria (e.g., A.5.1, CC6.1). This ensures that each control addresses requirements from both frameworks.
If your organization already has a SOC 2 assessment, about 43% of the evidence needed for ISO 27001 certification is likely already available. This catalog will help you identify areas of overlap and efficiently reuse existing evidence.
Use the control catalog as a single source of truth for both internal teams and auditors. It can guide policy updates, technical implementations, and evidence collection. For controls that don’t align perfectly between the two frameworks - such as SOC 2 Privacy criteria or specific ISO 27001 ISMS governance clauses - determine whether existing controls can be enhanced to cover these gaps. This approach avoids creating entirely separate processes.
Tools like ISMS Copilot can simplify this process with prebuilt mappings between ISO 27001 Annex A and SOC 2 criteria, as well as templates for risk assessments and control descriptions. Such tools help ensure your documentation remains consistent across both standards, keeping your compliance efforts organized and efficient.
Aligning ISMS and SOC 2 Operations
ISMS Documentation and SOC 2 Evidence Alignment
Use your ISO 27001 ISMS as the foundation for managing both ISO 27001 and SOC 2 requirements by centralizing policies, procedures, and control descriptions into a single, well-organized repository.
Start with your Statement of Applicability (SoA). This document outlines each ISO 27001 control and its implementation status. Add a column to the SoA to map each control to the relevant SOC 2 Trust Services Criteria. For instance, link ISO 27001 control A.9.2.3 with SOC 2 criterion CC6.2. This cross-referencing avoids duplication and streamlines evidence collection.
Write policies in neutral terms to serve both frameworks. For example, create one access control policy that addresses least privilege, periodic reviews, and provisioning workflows. Tag this policy in your document index with both "ISO 27001 A.9" and "SOC 2 CC6" references. When auditors ask for your access control policy, you can provide a single document backed by consistent evidence, such as quarterly access review reports, provisioning tickets, and deprovisioning logs.
Adopt a clear naming convention for evidence files, such as "CC6.2_A.9.2.3_Q1-2025_AccessReview.pdf", to indicate the controls covered. Store all documentation in a version-controlled repository with organized folders. This approach allows you to collect evidence once and reuse it for both audits, cutting redundant work by about 40%.
Finally, align your internal review processes to support this unified documentation structure.
Internal Audit and Review Integration
Develop a single, risk-based audit program that links each review to both ISO 27001 clauses and SOC 2 criteria. Use one issue log to record findings, tagging relevant controls for both frameworks. For example, a change management audit could simultaneously evaluate ISO 27001 A.12.1.2 and SOC 2 CC8.1 by examining the same set of change tickets. This method ensures that auditors can assess whether changes were properly approved, tested, and documented for both standards.
When issues are resolved, the corrective actions and their verification serve as evidence for both frameworks, minimizing disruptions and lowering audit costs.
Combine management review sessions to discuss risk profiles, incident trends, and control performance for both ISO 27001 and SOC 2. Meeting minutes and action logs from these sessions provide clear, unified evidence for oversight under both standards.
Once unified audits are in place, shift your focus to continuous improvement.
Continuous Improvement and Corrective Action
After completing unified audits, address any identified deficiencies promptly to maintain compliance. Use a single corrective-action workflow to manage issues under both ISO 27001 and SOC 2. Each issue record should include the source (e.g., internal audits, monitoring alerts, or customer feedback), document the impact and risk, provide a root-cause analysis, and outline corrective actions with assigned owners and deadlines.
For example, if orphaned accounts are identified, record them under A.9.2.5 and CC6.1. Once resolved, the updated logs can serve as evidence for both frameworks.
In the event of a security incident or a significant near miss, conduct structured post-incident reviews. These reviews should document lessons learned, update risk assessments, and adjust policies or system configurations as needed. Tracking these actions in a unified issue log demonstrates your commitment to improvement and satisfies the requirements of both ISO 27001 and SOC 2.
Leverage GRC tools to automate evidence collection, reminders, and dashboards. AI-powered assistants like ISMS Copilot can help by designing harmonized policies, suggesting control mappings, generating audit-ready narratives, and identifying evidence gaps. Integrations with HR, identity and access management (IAM), ticketing, and cloud platforms can further streamline evidence capture, enabling smaller teams to maintain strong compliance without adding extra staff.
Streamlining Evidence, Testing, and Audit Timelines
Evidence Repository and Reuse
Create a centralized repository to store all compliance evidence in one place, tagging each artifact for every relevant framework. According to A-LIGN, organizations that complete a SOC 2 assessment already meet about 43% of the evidence requirements for ISO 27001. By mapping artifacts once, you can cut down on duplicate uploads and make evidence collection much more efficient.
Organize your repository with detailed metadata for each artifact. Include information such as the ISO 27001 control reference (e.g., A.9.2.3), the SOC 2 Trust Services Criteria (e.g., CC6.x), the control owner, the date range the artifact covers, and the type of evidence (e.g., policy, log export, screenshot, or ticket). For example, a quarterly privileged-access review report covering January 1–March 31, 2025, could meet ISO 27001 Annex A.9 requirements and SOC 2 controls if it includes details like the reviewer’s name, scope, decisions, and timestamps. By tagging this report for both frameworks, you only need to store it once.
A master control and evidence matrix is a valuable tool for planning and audits. It lists each control, the required artifacts, and the frameworks they satisfy, making it easy to track what’s needed and where it applies.
Testing Cadences and Audit Scheduling
Once your evidence is centralized, the next step is to standardize testing and audit schedules. Align testing cadences with the most stringent frequency requirements. For example, conduct quarterly vulnerability scans and use the results to meet the requirements for multiple frameworks. Apply this approach to other recurring tasks like user access reviews, backup tests, incident response exercises, disaster recovery tests, security awareness training, and vendor risk assessments.
Coordinate external audit timelines to ensure that reviews for SOC 2 and ISO 27001 cover the same operating period. A multi-year compliance calendar can help align ISO 27001 certification milestones with annual SOC 2 cycles, simplifying long-term planning. To minimize disruptions, cluster audit fieldwork into a two- to four-week window and avoid scheduling during high-stakes business events, like product launches or fiscal year-end.
Leverage automation tools to stay on top of deadlines. Use a GRC platform to schedule tasks - like “Upload Q2 vulnerability scan report by July 15, 2025” - and integrate feeds from HR systems, ticketing platforms, SIEM, and cloud services. AI-powered tools, such as ISMS Copilot, can assist in creating unified testing checklists, mapping controls across frameworks like ISO 27001 and SOC 2, and identifying evidence gaps. This kind of automation allows smaller teams to maintain robust compliance without adding extra staff.
sbb-itb-4566332
Using Technology and Automation for Harmonization
Technology for Unified Compliance Efforts
Modern GRC platforms simplify compliance by managing ISO 27001 and SOC 2 within a single workspace, using a shared control library to map controls across both standards. These platforms include features like centralized policy and document management with version control, automated workflows for tasks like risk assessments and internal audits, and real-time dashboards to monitor readiness for both frameworks.
Automation plays a key role by integrating with systems like HR, cloud platforms, and logging tools to gather evidence such as access reports, configuration baselines, vulnerability scans, and tickets. For instance, a quarterly access review export can meet the requirements of both ISO 27001 and SOC 2. Automated reminders ensure that evidence collection aligns seamlessly with audit cycles.
The benefits of automation are clear: organizations can reuse around 40% of evidence, significantly cut down audit timelines, and reduce the number of findings. Automated task assignments and alerts further help lower audit fees and internal labor costs. These efficiencies pave the way for advanced tools like ISMS Copilot to take unified compliance efforts to the next level.
Using ISMS Copilot for Harmonized Compliance
ISMS Copilot builds on these automated compliance strategies by acting as an AI-powered assistant that simplifies policy creation and risk management. It generates and maintains policies, procedures, and standards that simultaneously address ISO 27001 Annex A controls and SOC 2 criteria. Drawing on expertise across more than 30 frameworks, ISMS Copilot creates a unified policy set covering critical areas like information security, access control, incident response, and change management. By using a single model to generate policies, organizations can eliminate inconsistencies between ISO- and SOC 2-focused documents, reducing audit risks and streamlining updates.
The tool also supports a unified risk management approach that satisfies ISO 27001’s structured risk management requirements and SOC 2’s focus on identifying and mitigating risks. It helps define risk criteria, scales for likelihood and impact, and treatment strategies, enabling a single risk register to meet the needs of both standards. ISMS Copilot can even propose risk statements tailored to common U.S. business contexts, like cloud-based SaaS models, remote teams, and third-party dependencies. It maps these risks to relevant controls and assists in creating risk assessment reports and treatment plans that align with both ISO 27001 and SOC 2.
Beyond risk management, ISMS Copilot provides ongoing support by analyzing logs, audit findings, and incident reports to draft root cause analyses, corrective action plans, and improvement initiatives that fulfill the requirements of both frameworks. When preparing for audits, the tool can simulate potential auditor questions, craft responses tied to specific controls and evidence, and refine key documentation like control environment descriptions and system overviews. This makes audit preparation smoother and more efficient, ensuring organizations are ready to meet compliance expectations without unnecessary complications.
ISO 27001 vs SOC 2: Do I Need Both?
Conclusion
Bringing ISO 27001 and SOC 2 together offers clear advantages: lower compliance costs, less audit fatigue, and quicker sales cycles. But this isn't just about checking boxes for audits - it’s about creating a more resilient and consistent security framework. This approach helps close real security gaps while supporting ongoing improvements in areas like risk management, access control, and incident response.
Think of this checklist as your operational guide for keeping harmonization on track. Review it every quarter to ensure that scope, risk assessments, control mapping, evidence reuse, and technology support remain aligned with your goals. By embedding these items into regular governance activities - such as quarterly business reviews, annual risk assessments, and scheduled internal audits - you can make harmonization a routine part of your management process rather than a one-off task.
Once your operations are aligned, technology and automation can take your harmonization efforts to the next level. Modern tools simplify the process by centralizing controls, automating evidence collection, and providing real-time insights. For example, platforms like ISMS Copilot can generate aligned policies, risk registers, and control descriptions from a single prompt. They can also map existing SOC 2 controls to ISO 27001 requirements and suggest reusable evidence, leveraging advanced automation to save time and effort.
Start by assessing your current efforts: list out your existing SOC 2 controls, ISO 27001 policies, and audit schedules to find areas of overlap. From there, create a unified template for control and evidence mapping, assigning clear ownership and deadlines. Finally, test out technology solutions - whether it’s a dedicated compliance platform or an AI assistant like ISMS Copilot - to automate at least one process, such as policy creation or control mapping. These steps will help you build a stronger compliance program.
The benefits of harmonization extend across your organization. Executives gain streamlined, consolidated insights into risk and control performance. Security teams can focus more on reducing risks and less on repetitive evidence formatting. Auditors experience smoother processes with clearer documentation and control designs, reducing back-and-forth communication. Unified reporting and evidence reuse, as outlined earlier, pave the way for a more effective compliance program. This approach not only strengthens trust but also accelerates deal cycles and positions your organization for success in competitive U.S. markets.
FAQs
How does aligning ISO 27001 and SOC 2 help lower compliance costs?
Aligning ISO 27001 with SOC 2 can help cut compliance costs by reducing duplicated efforts and addressing overlapping requirements in a single, cohesive approach. By bringing these frameworks together, you can simplify processes, eliminate repetitive controls, and create unified policies that meet the needs of both standards. This approach not only saves time but also optimizes the use of resources during audits and ongoing compliance management.
When done right, this alignment results in a more efficient compliance strategy. It reduces the need for separate audits and allows your team to concentrate on what truly matters - maintaining a robust and effective security posture.
How can organizations align risk management practices between ISO 27001 and SOC 2?
To bring risk management practices in line with both ISO 27001 and SOC 2, focus on developing a combined risk assessment process that meets the needs of both frameworks. Identify overlapping controls to reduce duplication and maintain a consistent approach across both standards. Incorporate unified risk treatment plans to address identified risks effectively, and ensure that well-organized, consistent documentation is available for audits and ongoing compliance efforts.
Using tools like ISMS Copilot can make this process easier by providing customized guidance and resources, enabling you to streamline compliance tasks with improved precision and efficiency.
How can tools like ISMS Copilot help streamline compliance with both ISO 27001 and SOC 2?
Tools like ISMS Copilot make aligning ISO 27001 and SOC 2 compliance far more manageable by providing AI-driven support tailored to both frameworks. It takes care of essential tasks like drafting policies, generating documentation, and performing risk assessments, cutting down on time and minimizing mistakes.
With its advanced AI capabilities, ISMS Copilot ensures consistency between the two frameworks, allowing compliance professionals to handle overlapping requirements more effectively. This streamlined approach helps maintain precision and keeps the process focused, making it easier to coordinate efforts and meet compliance goals with assurance.

