Staying compliant is non-negotiable for startups in the U.S., especially with frameworks like SOC 2, ISO 27001, HIPAA, and CCPA. Without clear policies and tools, compliance becomes a costly, time-consuming burden. Here’s the deal:
- Why compliance matters: Avoid penalties like $50,000+ fines for HIPAA violations or 4% of global revenue under GDPR. Non-compliance can also lead to data breaches costing $4–10 million and loss of customer trust.
- Automation saves time: Startups spend 40–60% of security resources on manual compliance tasks. Automation tools cut this effort by up to 80%, ensuring audit readiness and reducing delays.
- Key policies to have: Focus on an Information Security Policy, Access Control Policy, and Incident Response Policy. These are must-haves for frameworks like SOC 2 and ISO 27001.
- How automation helps: Tools like ISMS Copilot generate policies, automate evidence collection, and monitor compliance gaps - speeding up audits and reducing errors.
Compliance doesn’t have to be overwhelming. With the right tools and a structured checklist, you can protect your startup, build customer trust, and scale securely.
How to Achieve SOC 2 Compliance For $20K or Less
Required Policies for Startups
If you're a U.S. startup aiming for SOC 2 or ISO 27001 compliance, having the right written policies is non-negotiable. These policies aren't just for passing audits - they also reassure investors that your business takes security seriously. Auditors will look for documented commitments to areas like security, access control, and incident management. While SOC 2 allows flexibility in naming and structuring policies (as long as they align with the Trust Services Criteria), ISO 27001 has more specific requirements tied to its Annex A controls. At a minimum, you'll need an Information Security Policy, an Access Control and Identity Management Policy, and an Incident Response Policy. To strengthen your compliance framework, you should also consider policies for Acceptable Use, Change Management, Vendor Management, and Business Continuity.
Fortunately, modern compliance platforms can make this process smoother. Tools like ISMS Copilot can generate policy drafts tailored to your needs in minutes, leveraging expertise from over 30 compliance frameworks. Below, we’ll break down the key policies your startup needs to establish.
Information Security Policy
This is the cornerstone of your startup's security framework. An Information Security Policy outlines your organization's commitment to protecting data and serves as the foundation for both audit success and operational security. It should define the scope of your Information Security Management System (ISMS) - for example, specifying that it covers all customer data hosted in AWS US-East-1. The policy must detail which assets, processes, locations, and data types are included. To meet compliance requirements, it should be approved by top management (usually signed by the CEO, CTO, or CISO) and reviewed annually or whenever significant changes in technology, regulations, or business operations occur.
This policy supports ISO 27001 requirements (Annex A.5.1.1 and Clause 5.2) by establishing high-level security objectives and governance rules. For SOC 2, it demonstrates the governance needed to meet security criteria (CC6.1). To be effective, it should also outline roles and responsibilities, your approach to risk management, and how it connects to other supporting policies. Using automation tools with pre-built policy templates can help ensure that requirements for both frameworks are met without duplicating efforts.
Access Control and Identity Management Policy
Controlling who can access your systems and data is critical. An Access Control and Identity Management Policy ensures your startup enforces proper security boundaries. This policy must follow the principle of least privilege, granting users only the access they need. It should also require multi-factor authentication (MFA) for all accounts, especially for administrative and remote access. Implementing single sign-on (SSO) for centralized authentication and logging can further enhance security. Additionally, the policy should mandate regular access reviews - typically conducted quarterly - where managers and system owners verify that user permissions are still appropriate.
This policy addresses key requirements for ISO 27001 (Annex A.9) by covering user registration, privilege management, and periodic reviews. For SOC 2, it aligns with logical access security criteria (CC6.2–6.3). Automation tools that integrate with identity providers can make this process more efficient, reducing manual errors and maintaining detailed audit trails.
Incident Response Policy
When a security incident occurs, your team needs a clear plan to detect, respond to, and recover from it. An Incident Response Policy outlines these processes in detail. It should include severity classifications (e.g., low, medium, high, critical) based on the impact on data and business operations. The policy must also define escalation procedures - such as who gets notified and within what timeframe (e.g., within one hour for high-severity incidents). Additionally, it should specify breach notification rules and require post-incident analysis, like a root cause report completed within 30 days.
For ISO 27001, this policy satisfies incident response requirements (Annex A.16). For SOC 2, it covers detection, response, and external communication criteria (CC7). U.S. startups also need to comply with state and federal breach notification timelines. Automation platforms can integrate with communication tools to ensure notifications are sent on time, track response SLAs through dashboards, and maintain evidence for audits.
How to Automate Policy Management
Once you've drafted your core policies, the real work begins: keeping them updated, ensuring the right people have access, tracking employee sign-offs, and gathering compliance evidence. As your startup grows, managing policies manually can quickly become overwhelming. Automation simplifies this process by centralizing documents, scheduling reviews, tracking sign-offs, and continuously monitoring for compliance gaps. Modern compliance platforms can even integrate with your existing systems to automatically collect evidence and send alerts when configurations fall out of sync. Here’s how automation can make a difference in three critical areas:
Policy Lifecycle Management
Relying on manual processes to manage policies can lead to mistakes and inefficiencies. Automation tools centralize all your policies in one secure location with role-based access, so only authorized individuals can view sensitive documents. These platforms also create an audit trail by logging changes with timestamps. Automated reminders ensure policies remain current, with notifications sent via email or Slack to policy owners and approvers. Some tools even assign policies based on roles and flag gaps when regulations change. Additionally, pre-built policy libraries aligned with key standards can help you set up a baseline program in just days.
ISMS Copilot takes this process a step further by using AI to draft customized policies in minutes. It offers robust version control with change logs and schedules automated review reminders tailored to specific framework requirements. The platform also tracks employee sign-offs using integrated digital workflows, ensuring compliance across more than 30 frameworks with high precision. Instead of starting policies from scratch or tweaking generic templates, you can ask ISMS Copilot to draft an Acceptable Use Policy aligned with ISO 27001 Annex A.8.1.3 and SOC 2 CC6.1. From there, you can push it through your review and approval workflow - all within the same system. This approach can cut down manual authoring and coordination time by as much as 70–80%.
Evidence Collection and Monitoring
Efficient evidence collection is crucial for audit readiness, but doing it manually is both tedious and error-prone. Automation tools integrate with your cloud infrastructure (like AWS, GCP, or Azure), HR systems (such as BambooHR or Workday), identity providers (like Okta or Google Workspace), code repositories (such as GitHub or GitLab), and ticketing tools (like Jira). These integrations allow the platform to automatically pull evidence at scheduled intervals. Continuous monitoring replaces one-time checks with constant scans for issues like unpatched systems, excessive permissions, or publicly accessible storage buckets. For example, if a new admin account is created without multi-factor authentication, the system sends real-time alerts via email or Slack and updates dashboards to reflect the compliance status of key controls.
Some tools go even further by scanning for missing security patches, monitoring user activity to enforce least privilege, and providing real-time risk insights across your infrastructure. Unified audit dashboards simplify evidence gathering and ensure you’re always prepared for audits, eliminating the last-minute scramble to collect proof when an assessment is due.
Policy Training and Attestation
Even with automation, employee training and attestation are essential to ensure policies are followed in practice. Employees need to be aware of the policies that apply to them. Automation helps by assigning security awareness training, phishing simulations, and role-specific courses based on job functions. It also sends reminders for overdue or incomplete modules. When a new policy is introduced or an existing one is updated, the platform automatically distributes it to relevant employees and tracks digital acknowledgments, creating an auditable record of who has signed off and when. Escalation paths ensure that managers are notified if team members fail to complete required training within a set timeframe, such as 14 days. On-demand reports provide instant visibility into training completion rates and highlight any gaps that need addressing before assessments.
Many platforms also include features for rolling out policies with guided walkthroughs and pre-built libraries aligned with key frameworks. This reduces the workload for HR and security teams, ensures consistent training across distributed teams, and generates the documentation needed to meet requirements like ISO 27001 Annex A.7.2.2 (information security awareness) and SOC 2 CC1.4 (commitment to competence). For example, when an auditor asks for proof that all employees completed their annual security training, you can generate the necessary report in seconds instead of spending weeks tracking down records.
sbb-itb-4566332
Startup Readiness Checklist
Before diving into policies and tools, it’s crucial to lay out a clear roadmap. A structured checklist helps you figure out what needs protection, who’s responsible, and where automation will have the biggest impact. Without this groundwork, you risk creating a compliance program that’s either too narrow - leaving critical systems exposed - or too broad, wasting time and resources on unnecessary controls. The steps below will guide you in scoping your program, assigning responsibilities, and prioritizing automation.
Defining Compliance Scope and Frameworks
The first step is cataloging your startup's data types. This includes customer data like names, emails, and addresses (PII); payment card data (PCI); protected health information (PHI); and sensitive internal data such as source code or trade secrets. Map each data type to its storage location - AWS production accounts, staging environments, SaaS tools, code repositories, or vendor systems. This inventory becomes the backbone of your compliance scope, ensuring you include all relevant systems in audits.
Next, identify which compliance frameworks apply based on your business model and customer needs. For U.S. B2B SaaS companies targeting enterprise clients, SOC 2 Type II is a common starting point. If you handle health data, HIPAA compliance is a must. Companies processing payment card information need to adhere to PCI DSS, and those serving EU users must comply with GDPR. For global or security-conscious customers, ISO 27001 is often pursued for its structured approach to information security. Review investor due diligence documents and customer security questionnaires early - they often outline the frameworks your company is expected to meet.
Once you’ve identified the right frameworks, define your scope boundaries. Clearly list in-scope systems like production workloads, CI/CD pipelines, corporate laptops, identity providers, and HR systems. Exclude systems like marketing sandboxes or personal development environments. Document this scope with a formal statement, data flow diagrams, and a system inventory. These artifacts are essential for configuring automation tools to collect evidence and monitor compliance.
AI-powered tools like ISMS Copilot can simplify this process. They help map your technologies and data flows to frameworks such as ISO 27001, SOC 2, and NIST 800-53. Instead of manually cross-referencing control requirements, these tools identify applicable controls for your systems and data types, generate aligned policies, and highlight overlaps where one control satisfies multiple frameworks. This saves time and reduces redundant work right from the start.
With your scope and frameworks in place, the next step is assigning ownership to ensure accountability across your compliance program.
Assigning Policy and Automation Ownership
Accountability is key to keeping compliance efforts on track. Without clear roles, progress stalls because no one knows who’s responsible for drafting policies, managing tools, or responding to alerts. Start by designating an executive sponsor, typically your CEO or CTO. This person sets the risk tolerance, approves the scope, allocates resources, and signs off on policies. They also communicate the importance of compliance to investors and the team.
Next, appoint a compliance lead - often a Security Lead, CISO, or Operations Manager - who will oversee day-to-day progress, manage the roadmap, and handle the external auditor relationship. This person selects frameworks, configures automation tools, and tracks readiness milestones.
Assign control owners for specific areas:
- Engineering or DevOps: Cloud security, change management, logging, monitoring, backups, and disaster recovery.
- IT: Endpoint security, single sign-on (SSO), mobile device management (MDM), and account provisioning.
- HR or People Operations: Onboarding, offboarding, background checks, and training attestations.
- Legal or Finance: Vendor risk, data processing agreements, and regulatory filings.
Each control owner should have measurable KPIs, like time to resolve critical alerts or the percentage of systems with logging enabled. For automation, designate a tool owner - usually the compliance lead - to manage integrations, update scope, and coordinate with vendors. Assign technical owners for key systems: DevOps for cloud platforms (AWS, GCP, Azure), IT for identity providers (Okta, Azure AD), HR for HRIS systems, and Engineering for ticketing tools like Jira.
Document these responsibilities in a RACI matrix that maps processes (e.g., access reviews, incident management) to roles, ensuring clarity on who’s responsible, accountable, consulted, and informed. Regular standups with these owners can help address policy gaps or integration issues early on.
With ownership established, the next focus is on prioritizing automation efforts that deliver the best results quickly.
Prioritizing Automation Implementation
Not every control needs automation immediately. A risk-based approach helps you focus on high-impact, low-effort automations that auditors rely on and that protect your most sensitive data. Key priorities include:
- Automated evidence collection from critical systems.
- Identity management automation: SSO, multi-factor authentication (MFA), provisioning/deprovisioning, and periodic access reviews.
- Continuous monitoring and alerting for misconfigurations, open security groups, missing patches, and logging gaps.
- Policy distribution and training automation: Assign role-based policies and track attestations.
In the medium term (around six months), expand to include:
- A centralized risk register: Automatically pull inputs from vulnerability scans and track mitigation tasks with deadlines.
- Vendor risk management workflows: Automate security questionnaires, contract tracking, and renewal reminders.
- Change management automation: Integrate with ticketing and CI/CD pipelines to document code reviews and approvals.
For the long term (beyond the first year), focus on advanced capabilities like:
- Disaster recovery and business continuity testing: Automate backup restores and track DR test results.
- Advanced reporting dashboards: Monitor framework coverage, control health trends, and board-level metrics.
- Use tools like ISMS Copilot to streamline overlapping controls across frameworks like ISO 27001, SOC 2, and NIST, improving efficiency.
This phased approach balances early wins with long-term goals, addressing key audit and security risks while keeping the workload manageable. By focusing on the most impactful automations first, you can build a strong foundation that meets investor and customer expectations.
Balancing Automation with Validation
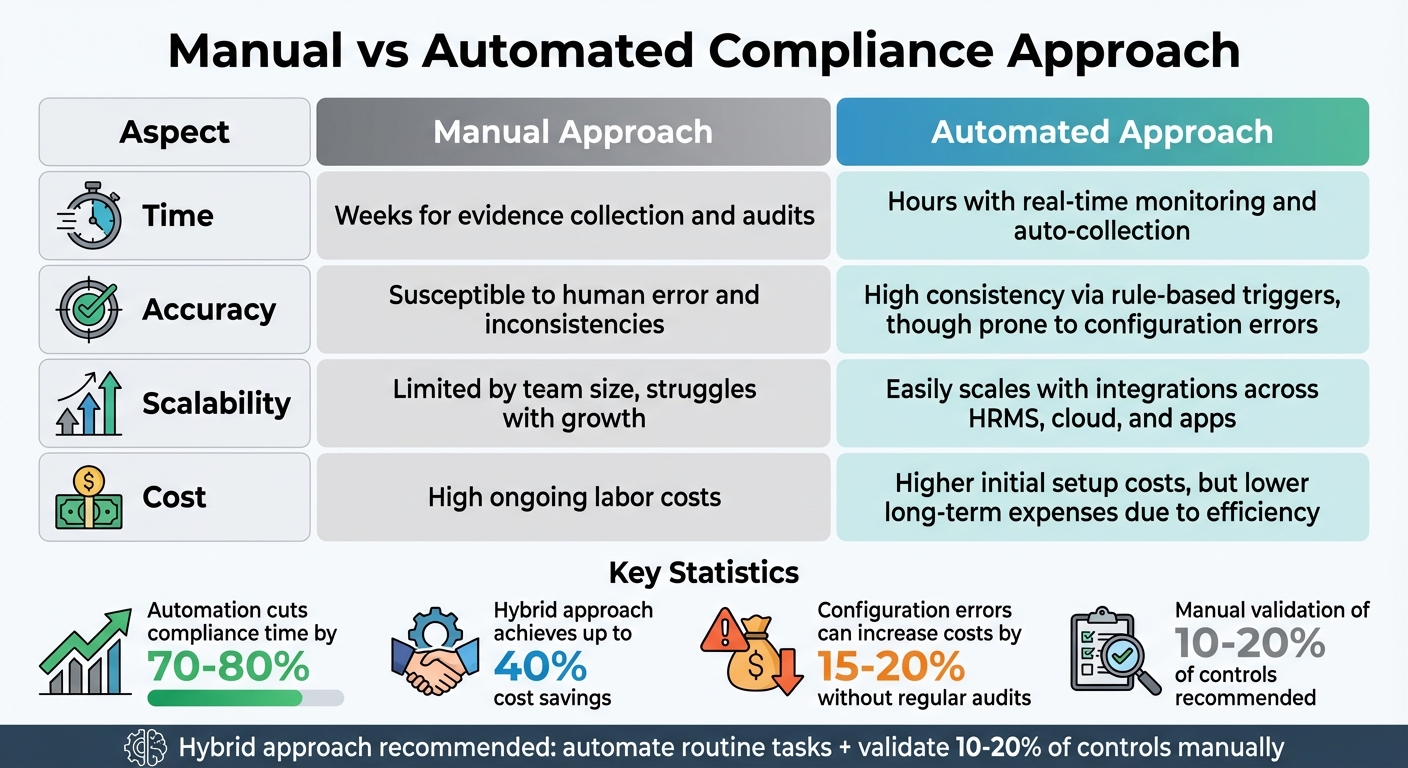
Manual vs Automated Compliance: Time, Cost, and Accuracy Comparison
While automation offers undeniable efficiency, it’s crucial to pair it with manual oversight to ensure accuracy. Automation can speed up compliance tasks and reduce errors, but it’s not foolproof. Startups that lean too heavily on automated tools without proper checks risk overlooking gaps, misconfiguring systems, or generating flawed audit evidence. The key is striking a balance: let automation handle repetitive tasks while relying on human expertise for strategic decisions and accuracy checks. Let’s explore how regular validation strengthens automated systems.
Benefits and Risks of Compliance Automation
Automation brings clear advantages to compliance efforts. Real-time monitoring drastically reduces the time needed for evidence collection, rule-based logic ensures consistent checks across frameworks like ISO 27001 and SOC 2, and centralized dashboards simplify reporting for auditors and stakeholders.
| Aspect | Manual Approach | Automated Approach |
|---|---|---|
| Time | Weeks for evidence collection and audits | Hours with real-time monitoring and auto-collection |
| Accuracy | Susceptible to human error and inconsistencies | High consistency via rule-based triggers, though prone to configuration errors |
| Scalability | Limited by team size, struggles with growth | Easily scales with integrations across HRMS, cloud, and apps |
| Cost | High ongoing labor costs | Higher initial setup costs, but lower long-term expenses due to efficiency |
However, automation isn’t immune to risks. Configuration errors or failed integrations can increase costs by 15-20% if not addressed through regular audits. While automation can cut compliance time by 70-80%, without validation, errors can raise the risk of failure by 25%. A hybrid approach - automating routine tasks while manually validating 10-20% of controls - can achieve up to 40% cost savings over time without compromising accuracy.
Validation and Internal Audit
Automation’s benefits are amplified when paired with regular validation to ensure system integrity. Internal audits can identify issues before they escalate during external reviews. Start with monthly audits during the first six months of implementation, then transition to quarterly reviews as processes stabilize. A thorough validation checklist might include:
- Spot-checking 10-20% of automated evidence against source systems to verify accuracy.
- Testing integrations by simulating system failures and reviewing audit logs for manual overrides and exceptions.
- Conducting gap analyses to ensure control mappings align with relevant frameworks.
- Evaluating alert systems through mock incidents to test their effectiveness.
- Monitoring policy training completion rates, aiming for above 90% through automated tracking.
Document any exceptions or manual overrides in a centralized system with approval workflows. This audit trail is essential for regulatory reporting, proving to auditors that automation isn’t being blindly trusted. Unified dashboards can further simplify compliance by offering real-time visibility into control functionality, reporting accuracy, and risk coverage, eliminating the need for full manual re-audits.
Preparing for Investors and Customers
Combining automation with validation doesn’t just streamline compliance - it also builds confidence with stakeholders. Investors and enterprise customers want to see that compliance is taken seriously. Creating a trust center with customized dashboards can demonstrate real-time compliance status, automation coverage (aiming for 90% of controls automated), policy libraries mapped to frameworks like SOC 2 and ISO 27001, and up-to-date audit reports. Certifications like SOC 2 Type II can be shared securely through gated portals, showcasing transparency and continuous monitoring.
Tools like ISMS Copilot simplify this process by offering AI-powered policy drafts and audit-ready reports. Unlike general-purpose AI tools like ChatGPT, ISMS Copilot is specifically designed for compliance, providing structured outputs and deep knowledge of frameworks. This reduces manual validation efforts and makes it easier to showcase compliance accuracy during investor presentations and demos.
"ISMS Copilot accelerates compliance work by handling time-consuming tasks like policy writing and document analysis, but it's not a replacement for professional expertise. Use it to speed up your workflow, get quick framework guidance, and generate first drafts - while you focus on strategic decisions and client relationships."
- ISMS Copilot
Always cross-check outputs from automated tools against official documentation. Automation is a powerful assistant, but it’s not a substitute for human expertise. By combining speed and consistency with hands-on oversight, you can build a scalable compliance program that earns the trust of auditors, investors, and customers alike.
Conclusion
Creating a compliance program from the ground up can feel overwhelming, but with a clear plan and the right tools, it becomes much more manageable - even for small, fast-moving startup teams. Start by defining your compliance scope, selecting the frameworks you’ll follow, and establishing core policies. Assign clear ownership for each policy and automation task to ensure nothing gets overlooked as your company grows. This groundwork sets the stage for effectively using automation.
Automation takes compliance from being a series of manual, periodic tasks to a system of continuous monitoring. Tools that handle evidence collection, policy distribution, training attestations, and real-time monitoring can dramatically cut down on repetitive work. This allows your team to focus on strategic decisions rather than getting bogged down in spreadsheets. Platforms like ISMS Copilot, which support over 30 frameworks, offer AI-powered features like policy drafting, control mapping, and audit-ready reporting. These tools can help startups move quickly without sacrificing accuracy. However, even the best automation tools need human oversight.
Automation isn’t a set-it-and-forget-it solution. It works best when paired with internal audits and regular validation. This means checking for configuration errors, testing integrations, and ensuring your controls perform as expected. Continuous monitoring should go hand-in-hand with periodic audits. For example, review a sample of automated evidence, simulate potential failures, and document any exceptions. Combining automated workflows with manual validation builds trust with auditors and ensures your compliance program remains reliable.
For U.S. startups, compliance isn’t just about meeting regulatory requirements - it can be a competitive advantage. Real-time dashboards and certifications like SOC 2 Type II can enhance investor and customer confidence. By maintaining an up-to-date checklist, using purpose-built tools, and balancing speed with careful oversight, you can scale securely while turning compliance into a strategic asset for your business.
FAQs
How does automation help startups save on compliance costs?
Automation offers startups a way to cut down compliance costs by handling labor-intensive tasks such as drafting policies, conducting risk assessments, and keeping documentation up to date. By reducing the need for manual effort and costly external consultants, it provides a more efficient solution.
With these processes simplified, startups can redirect their energy and resources toward growth. At the same time, automation ensures compliance is managed with greater precision and efficiency, making it a win-win for both cost savings and operational accuracy.
What key policies are required for achieving SOC 2 and ISO 27001 compliance?
To achieve compliance with SOC 2 and ISO 27001, startups must create and enforce key policies that address essential aspects of information security and risk management. These policies serve as the foundation for safeguarding data and ensuring operational integrity. Here are some critical ones:
- Information Security Policy: Sets the organization's overall strategy and commitment to maintaining security standards.
- Access Control Policy: Establishes rules for managing and restricting access to systems and sensitive data.
- Incident Response Policy: Lays out the steps for identifying, addressing, and mitigating security incidents effectively.
- Data Protection and Privacy Policy: Ensures adherence to privacy laws and protects sensitive information from unauthorized access or misuse.
- Business Continuity and Disaster Recovery Policy: Prepares the organization to handle disruptions and ensures recovery plans are ready to minimize downtime.
In addition to these, policies covering Risk Management, Vendor and Third-Party Management, and Acceptable Use are equally essential for comprehensive compliance. Leveraging tools like ISMS Copilot can streamline these processes, making it easier to implement and maintain consistency across frameworks.
How does ISMS Copilot help ensure your startup is always ready for audits?
ISMS Copilot simplifies the process of preparing for audits by creating customized, audit-ready policies and procedures that fit your specific compliance requirements. It offers expert recommendations grounded in practical compliance situations, ensuring your documentation stays aligned with standards like ISO 27001.
Equipped with tools like structured workspaces and document analysis features, ISMS Copilot helps you stay efficient and organized, reducing the stress of audits while improving reliability.

