Die Verwaltung mehrerer Cybersicherheits-Frameworks kann eine Herausforderung sein, aber das NIST Cybersecurity Framework (CSF) vereinfacht diesen Prozess. Durch die Angleichung an Standards wie ISO 27001, SOC 2 und FedRAMP unterstützt das NIST CSF Unternehmen dabei, die Compliance zu optimieren, Redundanzen zu reduzieren und das Risikomanagement zu verbessern.
Wichtigste Erkenntnisse:
- NIST CSF 2.0 (veröffentlicht im Februar 2024) führt sechs Kernfunktionen ein: Steuern, Identifizieren, Schützen, Erkennen, Reagieren und Wiederherstellen.
- Die Integration von NIST in Rahmenwerke wie ISO 27001 und SOC 2 verhindert doppelte Arbeit, da sich viele Anforderungen überschneiden.
- Tools wie ISMS Copilot automatisieren die Zuordnung von Kontrollen, die Sammlung von Nachweisen und die Erstellung von Richtlinien, was Zeit spart und Fehler reduziert.
Warum das wichtig ist: Unternehmen, die mehrere Compliance-Anforderungen unter einen Hut bringen müssen, können NIST CSF nutzen, um ihre Bemühungen zu vereinheitlichen, Audits zu vereinfachen und strengere Cybersicherheitspraktiken aufrechtzuerhalten.
Vorteile der Integration von NIST in andere Frameworks
Bessere Risikosichtbarkeit und -verwaltung
Durch die Integration von NIST in Rahmenwerke wie ISO 27001, SOC 2 und HIPAA können Unternehmen eine einheitliche Perspektive auf Cybersicherheitsrisiken schaffen. Die strukturierte Methodik von NIST – Steuern, Identifizieren, Schützen, Erkennen, Reagieren und Wiederherstellen – dient als gemeinsame Sprache, die verschiedene Compliance-Anforderungen miteinander verbindet. Dieser Ansatz ermöglicht es Sicherheitsteams, Schwachstellen effektiver zu lokalisieren und bedeutende Bedrohungen zu priorisieren, wodurch unnötige Warnmeldungen reduziert werden und der Fokus auf das Wesentliche gelegt werden kann.
Die Zuordnung von NIST-Kontrollen zu verschiedenen Standards ermöglicht eine kontinuierliche Risikobewertung und dynamische Überwachung von Bedrohungen, ohne dass zwischen verschiedenen Systemen gewechselt werden muss. Diese nahtlose Integration stellt sicher, dass Risikomanagementdaten direkt in umfassendere Unternehmensprozesse einfließen und der Unternehmensleitung einen klaren und konsistenten Überblick über den Cybersicherheitsstatus des Unternehmens verschaffen. Darüber hinaus reduziert dieser Ansatz redundante Dokumentationsaufgaben und optimiert den gesamten Risikomanagementprozess.
Weniger Doppelarbeit
Die NIST-Frameworks sind eng an regulatorische Anforderungen wie HIPAA, CMMC und PCI-DSS angelehnt, sodass Unternehmen gemeinsame Kontrollen für mehrere Standards einfacher anwenden können. Die Befolgung der NIST-Richtlinien gewährleistet umfassende Aufzeichnungen, die sich überschneidende Anforderungen erfüllen, sodass Sie mit minimalem Mehraufwand für Audits vorbereitet sind. Mit den einheitlichen Kontrollen des NIST können Sie mehrere Standards gleichzeitig erfüllen und müssen weniger doppelte Dokumentationen erstellen.
Diese Strategie „einmal testen, mehrfach anwenden“ ermöglicht es, mit einem einzigen Satz von Kontrollen gleichzeitig die Anforderungen mehrerer Audits zu erfüllen. So kann beispielsweise die Implementierung von Zugriffskontrollen gemäß NIST SP 800-53 die Anforderungen von ISO 27001, SOC 2 und HIPAA erfüllen, wodurch unnötige Wiederholungen über verschiedene Frameworks hinweg vermieden werden. Solche Maßnahmen sparen nicht nur Zeit, sondern verbessern auch die Compliance über verschiedene Regionen und Standards hinweg.
Stärkere globale Compliance und Sicherheit
Die weltweite Anerkennung des NIST und seine Querverweise auf Normen wie ISO/IEC 27001:2022 und SP 800-171 Revision 3 erleichtern es Unternehmen, grenzüberschreitende Compliance zu erreichen. Diese offiziellen Querverweise bieten klare Orientierungshilfen für die Navigation durch mehrere Rahmenwerke.
Unternehmen, die eine externe Validierung anstreben, können von SOC 2+-Berichten profitieren, die neben Rahmenwerken wie HIPAA, HITRUST und ISO auch NIST-Kontrollen berücksichtigen. Grant Thornton nutzt beispielsweise sein Automatisierungstool SOC.x, um Compliance-Prozesse zu optimieren, sodass Kunden mit einem einzigen, umfassenden Bericht die Anforderungen verschiedener Interessengruppen erfüllen können. Dieser integrierte Ansatz gibt Kunden, Aufsichtsbehörden und anderen Interessengruppen die Gewissheit, dass Ihr Unternehmen in der Lage ist, vielfältige Sicherheits- und Datenschutzanforderungen zu erfüllen.
Die 5 Schritte des NIST zur Einführung und/oder Integration des NIST Cybersecurity Framework 2.0 in Ihrem Unternehmen
Wichtige Rahmenwerke für die Integration mit NIST
Die folgenden Integrationen zeigen, wie die strukturierte Methodik des NIST die Compliance über mehrere Frameworks hinweg vereinfachen kann.
NIST und ISO 27001
Die Kernfunktionen des NIST – Identifizieren, Schützen, Erkennen, Reagieren und Wiederherstellen – stimmen nahtlos mit Anhang A der ISO 27001 überein, wodurch die internationale Zertifizierung effizienter wird. Beide Rahmenwerke konzentrieren sich auf risikobasierte Ansätze für die Informationssicherheit, und die detaillierten Leitlinien des NIST bilden eine solide Grundlage für die Entwicklung eines Informationssicherheits-Managementsystems (ISMS), das den Anforderungen der ISO 27001 entspricht.
Diese Angleichung ist besonders vorteilhaft für Organisationen, die weltweit tätig sind. ISO 27001 bietet eine international anerkannte Zertifizierung, während NIST detaillierte, praktische Leitlinien für die Umsetzung bereitstellt.
NIST und SOC 2
Für Unternehmen, die den nordamerikanischen Markt anvisieren, schafft die Integration von NIST und SOC 2 ein starkes Sicherheitsframework, das sowohl das interne Risikomanagement als auch die externe Kundensicherheit abdeckt. Untersuchungen zeigen eine erhebliche Überschneidung – etwa 60 bis 70 % – zwischen SOC 2 und NIST 800-53-Kontrollen, insbesondere in Bereichen wie Zugriffsmanagement, Incident Response und Risikobewertung.
Durch die Zuordnung der NIST-Kontrollen zu den SOC 2-Kriterien können Unternehmen ihre Sicherheitsmaßnahmen verstärken und gleichzeitig die Audit-Bereitschaft sicherstellen. Die Überschneidung reduziert den zusätzlichen Aufwand, da NIST die für die Umsetzung der Kontrollen erforderliche technische Tiefe bietet und SOC 2 die formelle Bescheinigung liefert, die Kunden und Partner häufig verlangen.
NIST und Bundesstandards (FedRAMP, CMMC)
Für Organisationen, die mit Bundesbehörden zusammenarbeiten oder kontrollierte, nicht klassifizierte Informationen (Controlled Unclassified Information, CUI) verwalten, ist die Einhaltung der NIST-Vorgaben unverzichtbar. NIST SP 800-53 ist für die FedRAMP-Zertifizierung unerlässlich, während NIST SP 800-171 die Grundlage für die CMMC-Konformität bildet. Diese Anpassungen sind regulatorische Notwendigkeiten.
Der Vorteil liegt auf der Hand: Durch die Implementierung von NIST-Kontrollen können Unternehmen mehrere bundesstaatliche Anforderungen gleichzeitig erfüllen. So können Auftragnehmer beispielsweise NIST SP 800-171 nutzen, um DFARS-Klauseln zu erfüllen und sich auf CMMC-Bewertungen vorzubereiten, wodurch die Bemühungen im Rahmen verschiedener bundesstaatlicher Compliance-Programme optimiert werden.
sbb-itb-4566332
Strategien für die Multi-Framework-Kontrollzuordnung
Manuelles vs. automatisiertes Compliance- Mapping: Wesentliche Unterschiede und Vorteile
Wenn Sie NIST in andere Frameworks integrieren, öffnen Sie die Tür zu reibungsloseren Compliance-Prozessen. Die meisten Cybersicherheits-Frameworks – wie ISO 27001, SOC 2, NIST CSF, NIS 2 und DSGVO – basieren auf ähnlichen Prinzipien und erfordern oft überlappende Nachweise. Auch wenn sich die Formulierungen unterscheiden mögen, bleiben die Kernanforderungen doch konsistent. Bei dieser Überschneidung kann strategisches Kontroll-Mapping einen echten Unterschied machen und Unternehmen dabei helfen, ihre Bemühungen über mehrere Standards hinweg aufeinander abzustimmen.
Verwendung gemeinsamer Steuerelemente
Gemeinsame Kontrollen sind Sicherheitsmaßnahmen, die gleichzeitig die Anforderungen mehrerer Rahmenwerke erfüllen. Diese Kontrollen bilden das Rückgrat Ihrer Compliance-Bemühungen. Bereiche wie Zugriffskontrolle und Identitätsmanagement, Incident Response, Backup und Recovery sowie Lieferantenmanagement tauchen häufig in verschiedenen Rahmenwerken auf. So kann beispielsweise ein gut konzipiertes Zugriffskontrollsystem gleichzeitig die Anforderungen von NIST, ISO 27001, SOC 2 und sogar Rahmenwerken wie HIPAA oder PCI DSS erfüllen.
Durch die Implementierung der CIS Critical Security Controls, die bereits auf NIST CSF, ISO/IEC 27001, SOC 2, HIPAA und PCI DSS abgestimmt sind, können Sie kontinuierlich Nachweise sammeln und wiederverwenden. Der Schlüssel liegt darin, diese Nachweise so zu organisieren, dass sie leicht auf verschiedene Frameworks angewendet werden können – damit sie sowohl nachvollziehbar als auch wiederverwendbar sind.
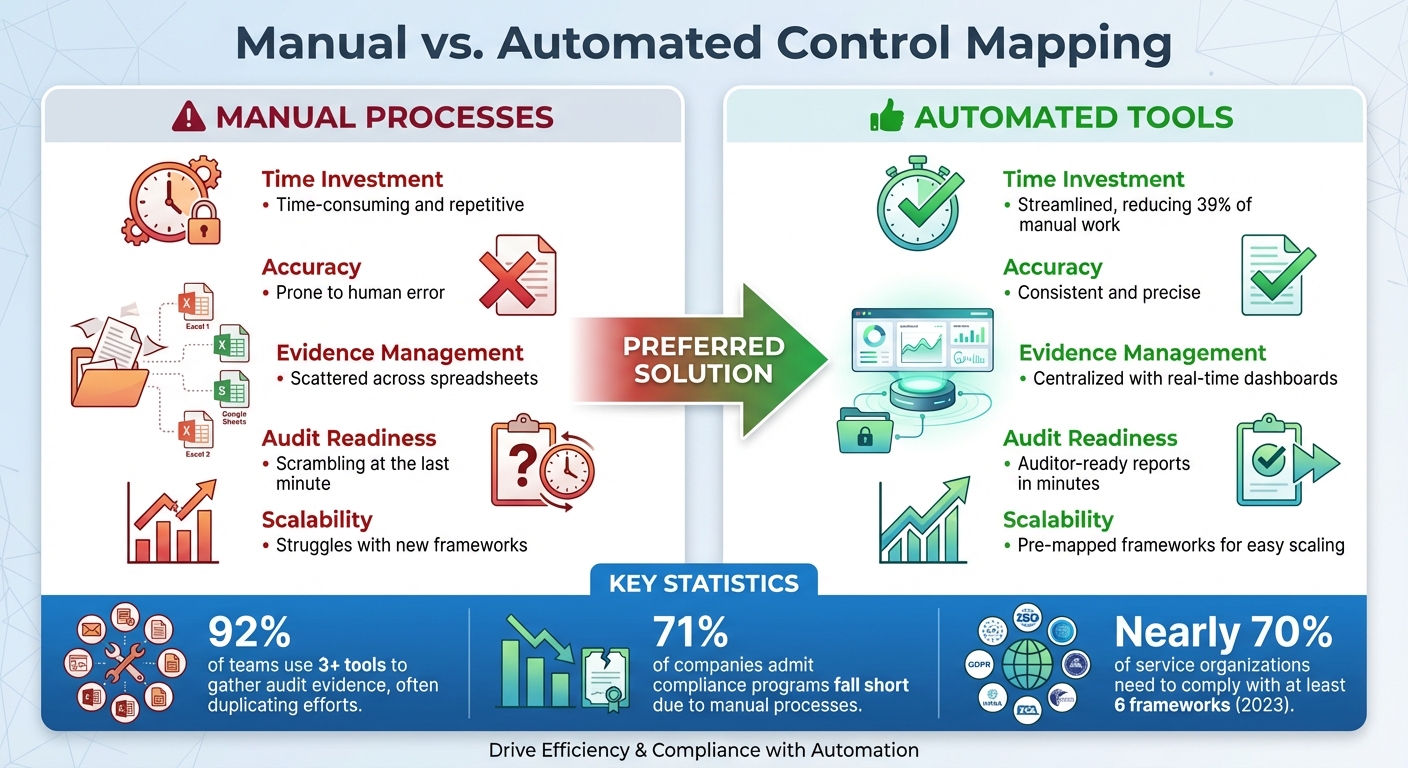
Manuelles vs. automatisiertes Mapping: Vor- und Nachteile
Die Entscheidung zwischen manueller und automatisierter Kontrollzuordnung ist von entscheidender Bedeutung. Da fast 70 % der Dienstleistungsunternehmen im Jahr 2023 mindestens sechs Rahmenwerke einhalten müssen, wird es immer schwieriger, manuelle Prozesse aufrechtzuerhalten. Die manuelle Zuordnung stützt sich oft auf unverbundene Tools, was sie zeitaufwändig und fehleranfällig macht. Sie bietet zwar vollständige Übersicht, ist aber ein mühsamer Prozess.
Andererseits zentralisieren automatisierte Tools wie ISMS Copilot das Kontrollmanagement, die Nachweise und die Zuordnungen an einem Ort. Diese Plattformen können Richtlinien, Protokolle und Berichte analysieren, um relevante Informationen zu extrahieren, die bestimmten Anforderungen entsprechen. Sie schlagen sogar Antworttexte vor und verknüpfen Nachweise mit den entsprechenden Kontrollen. Die Automatisierung erfordert jedoch eine Vorabinvestition in die Einrichtung und Feinabstimmung, um sie an die individuellen Anforderungen Ihres Unternehmens anzupassen.
| Aspekt | Manuelle Prozesse | Automatisierte Werkzeuge |
|---|---|---|
| Zeitaufwand | Zeitaufwendig und repetitiv | Optimiert, wodurch 39 % der manuellen Arbeit eingespart werden |
| Genauigkeit | Anfällig für menschliches Versagen | Konsistent und präzise |
| Beweismittelverwaltung | Über verschiedene Tabellen verteilt | Zentralisiert mit Echtzeit-Dashboards |
| Prüfungsbereitschaft | In letzter Minute noch schnell etwas zusammenstellen | In wenigen Minuten fertige Berichte für den Wirtschaftsprüfer |
| Skalierbarkeit | Schwierigkeiten mit neuen Rahmenbedingungen | Vorkonfigurierte Frameworks für einfache Skalierung |
Hier ist eine aussagekräftige Statistik: 92 % der Teams verwenden drei oder mehr Tools, um Audit-Nachweise zu sammeln, wodurch sich ihre Arbeit oft doppelt. Gleichzeitig geben 71 % der Unternehmen zu, dass ihre Compliance-Programme aufgrund der Abhängigkeit von manuellen Prozessen unzureichend sind. Diese Zahlen unterstreichen die Vorteile der Automatisierung und ihre Fähigkeit, die Compliance zu optimieren.
Beispiel für die Zuordnung von Steuerelementen über Frameworks hinweg
Sehen wir uns einmal an, wie die Zugriffskontrolle über mehrere Frameworks hinweg abgebildet werden kann. Diese zentrale Sicherheitsmaßnahme ist in fast allen wichtigen Frameworks eine Voraussetzung, auch wenn die Terminologie und der Schwerpunkt variieren können.
In NIST CSF 2.0 fällt die Zugriffskontrolle unter die Funktion „Schützen“, insbesondere Identitätsmanagement und Zugriffskontrolle (PR.AC). Bei ISO 27001 wird dies in Anhang A.9 (Zugriffskontrolle) behandelt, der dokumentierte Verfahren für die Bereitstellung und Entziehung von Benutzerzugriffen vorschreibt. SOC 2 deckt diesen Bereich ebenfalls unter den CC6-Kriterien (Logische und physische Zugriffskontrollen) ab und konzentriert sich dabei auf die Beschränkung des Zugriffs auf Systeme und Daten basierend auf Benutzerrollen.
Die Überschneidungen sind erheblich – allein zwischen den Kriterien von ISO 27001 und SOC 2 liegen sie bei etwa 80 %. Beispielsweise erfüllt die Implementierung einer Multi-Faktor-Authentifizierung (MFA) für alle Benutzerkonten gleichzeitig die Anforderungen von NIST CSF PR.AC-7, ISO 27001 A.9.4.2 und SOC 2 CC6.1. Dieselbe Kontrolle, die durch dieselben Nachweise (wie MFA-Protokolle, Screenshots und Zugriffsüberprüfungen) unterstützt wird, kann verwendet werden, um die Anforderungen aller drei Rahmenwerke zu erfüllen.
Dieser Ansatz vereinfacht nicht nur die Vorbereitung auf Audits, sondern gewährleistet auch Konsistenz. Durch die Erstellung eines einzigen, gut organisierten Nachweispakets, das mehreren Anforderungen zugeordnet ist, können Sie viel Zeit und Aufwand sparen und gleichzeitig einen hohen Compliance-Standard in Ihrem gesamten Unternehmen aufrechterhalten.
Bewährte Verfahren für die NIST-Integration
Die Integration des NIST-Frameworks in die Multi-Framework-Compliance erfordert strukturierte Tools, kontinuierliche Überwachung und abteilungsübergreifende Teamarbeit. Diese Vorgehensweisen bauen auf früheren Diskussionen über einheitliche Kontrollzuordnungen auf und zielen darauf ab, sowohl die Automatisierung als auch die Zusammenarbeit innerhalb von Organisationen zu verbessern.
Verwendung von ISMS Copilot für die Einhaltung mehrerer Rahmenwerke
ISMS Copilot vereinfacht die Herausforderungen der Compliance-Verwaltung über mehrere Frameworks hinweg, indem es Aufgaben wie Kontrollzuordnung, Richtlinienerstellung, Beweissammlung und Überwachung zentralisiert. Es ist immer auf dem neuesten Stand mit Frameworks wie dem NIST Cybersecurity Framework, NIST 800-53, ISO 27001 und SOC 2. Im Gegensatz zu allgemeinen KI-Tools wie ChatGPT oder Claude ist ISMS Copilot speziell auf Compliance-Aufgaben zugeschnitten und spart Zeit, indem es die Querverweise zwischen den Kontrollen von NIST 800-53 und anderen Standards automatisiert. Mithilfe eines Retrieval-Augmented-Generation-Ansatzes greift es auf einen kuratierten Compliance-Datensatz zurück, um auditorenfertige Antworten zu generieren.
Wenn Sie Richtlinien und Dokumentationen hochladen, identifiziert ISMS Copilot, wo Ihre bestehenden NIST-Kontrollen mit den Anforderungen von ISO 27001 oder SOC 2 übereinstimmen. Die Workspaces-Funktion organisiert Workflows nach Kunden oder Projekten und erleichtert so die Verwaltung mehrerer Standards. Die Plattform automatisiert wichtige Prozesse – Kontrollzuordnung, Beweissammlung und Richtlinienerstellung – und bietet gleichzeitig maßgeschneiderte Richtlinien und Abhilfemaßnahmen für alle erkannten Lücken. Mit diesen Tools sollte der nächste Schwerpunkt auf einer gründlichen Lückenanalyse und einer kontinuierlichen Überwachung liegen.
Durchführung von Gap-Analysen und kontinuierlicher Überwachung
Beginnen Sie damit, Ihre aktuelle Compliance-Situation anhand von NIST und anderen Frameworks zu bewerten, um Kontrolllücken zu identifizieren. Implementieren Sie anschließend eine kontinuierliche Überwachung, um Kontrollen in Echtzeit zu validieren. Das NIST National Online Informative References (OLIR)-Programm bietet offizielle Zuordnungen zwischen NIST CSF 2.0 und anderen Frameworks, wie NIST SP 800-53, NIST SP 800-171 und verschiedenen branchenspezifischen Richtlinien. Durch die Automatisierung der Beweissammlung und der Echtzeit-Kontrollvalidierung können Unternehmen von periodischen Audits zu einem kontinuierlichen Compliance-Modell übergehen und potenzielle Probleme erkennen, bevor sie zu Audit-Befunden eskalieren.
Zusammenarbeit mit Teams und Stakeholdern
Automatisierung ist nur ein Teil der Gleichung – erfolgreiche Compliance hängt auch von einer engen Zusammenarbeit ab. Multi-Framework-Compliance erfordert Beiträge von Teams aus den Bereichen Technik, Betrieb, Recht und Wirtschaft. Um Sicherheit in Entwicklungsprozesse zu integrieren, sollten Sie Verfahren wie Secure SDLC und DevSecOps einsetzen und Sicherheit als Kernelement der Technik und des Betriebs verankern. NIST CSF 2.0 bietet eine gemeinsame Sprache für die Diskussion von Risiken und Ergebnissen und verbessert so die Konsistenz bei der Risikoüberwachung und -anpassung im gesamten Unternehmen.
Organisationsprofile innerhalb von NIST CSF 2.0 sind besonders hilfreich, um Ihre aktuelle und angestrebte Cybersicherheitslage in einfachen Worten zu definieren und zu kommunizieren. Regelmäßige funktionsübergreifende Besprechungen können die Abstimmung hinsichtlich Risiken und Compliance-Zielen sicherstellen, sodass alle Beteiligten auf dem gleichen Stand sind.
Fazit und wichtigste Erkenntnisse
Zusammenfassend lässt sich sagen, dass die Umsetzung der zuvor beschriebenen Strategien Ihre Compliance-Bemühungen zu einem optimierten und effektiveren Prozess machen kann. Die Integration des NIST Cybersecurity Framework in Ihre Multi-Framework-Compliance-Strategie stärkt nicht nur Ihre Sicherheitsmaßnahmen, sondern vereinfacht auch die Anpassung an Standards wie ISO 27001, SOC 2 und FedRAMP. Dieses Framework hilft Ihnen dabei, Investitionen zu priorisieren und schafft eine einheitliche Methode zur Kommunikation von Risiken innerhalb Ihres Unternehmens.
Einer der Schlüssel zum Erfolg ist der Einsatz gemeinsamer Kontrollen und Automatisierung. Offizielle Zuordnungen zeigen, dass ein einziger Satz von Kontrollen die Anforderungen mehrerer Audits erfüllen kann. Dadurch werden redundante Aufgaben eliminiert, das Chaos der verstreuten Beweissammlung reduziert und Ihr Unternehmen von der Hektik der Last-Minute-Audits zu einer kontinuierlichen Compliance-Sicherung geführt.
ISMS Copilot ist ein herausragendes Tool in diesem Bereich, das Aufgaben wie Kontrollzuordnung, Beweissammlung und Richtlinienentwurf in mehr als 30 Frameworks automatisiert. Es wurde mit Blick auf die Compliance entwickelt und nutzt einen kuratierten Datensatz, um auditorenfertige Antworten zu erstellen und Dokumentationslücken aufzuzeigen. Unternehmen, die ähnliche KI-gesteuerte Lösungen einsetzen, haben die Vorbereitungszeit für Audits von Wochen auf nur wenige Stunden reduziert.
Durch die Kombination der strukturierten Methodik des NIST mit Automatisierung und Teamzusammenarbeit können Sie das ganze Jahr über auditbereit bleiben und Ihrem Sicherheitsteam ermöglichen, sich auf die Bekämpfung echter Sicherheitsbedrohungen zu konzentrieren. Die Multi-Framework-Compliance geht, wenn sie durchdacht angegangen wird, über das bloße Abhaken von Checklisten hinaus – sie fördert Vertrauen und stärkt Ihre allgemeine Sicherheit, indem sie ein breites Spektrum an Kontrollen abdeckt. Dieser einheitliche Ansatz erfüllt nicht nur die Compliance-Anforderungen, sondern trägt auch dazu bei, eine proaktive Sicherheitsmentalität zu entwickeln.
Beginnen Sie mit einer Lückenanalyse, führen Sie eine kontinuierliche Überwachung ein und nutzen Sie Automatisierung, um Ihre Nachweise zu organisieren. Auf diese Weise kann die Einhaltung mehrerer Rahmenwerke zu einem strategischen Vorteil werden, anstatt eine mühsame Aufgabe zu sein, und messbare Gewinne in Bezug auf Effizienz, Risikomanagement und Auditbereitschaft erzielen.
Häufig gestellte Fragen
Wie funktioniert NIST CSF 2.0 in Verbindung mit ISO 27001 und SOC 2 hinsichtlich der Compliance?
NIST CSF 2.0 wurde entwickelt, um mühelos mit anderen Cybersicherheitsstandards wie ISO 27001 und SOC 2 zusammenzuarbeiten, und bietet eine solide Grundlage für die Verwaltung der Compliance über mehrere Frameworks hinweg. Sein ergebnisorientiertes und modulares Design passt gut zu den in diesen Standards beschriebenen Prozessen und Kontrollen und trägt dazu bei, redundante Anstrengungen zu reduzieren.
Nehmen wir als Beispiel die Kernfunktionen des NIST CSF – Identifizieren, Schützen, Erkennen, Reagieren, Wiederherstellen. Diese lassen sich direkt den ISMS-Prozessen und den Kontrollen in Anhang A der ISO 27001 sowie den Trust Services Criteria in SOC 2 zuordnen. Diese Angleichung ermöglicht es Unternehmen, Kontrollimplementierungen über verschiedene Frameworks hinweg wiederzuverwenden. So können beispielsweise dieselben Kontrollen für das Asset-Management oder die Sicherheitsrichtlinien sowohl die Anforderungen von ISO 27001 als auch von SOC 2 erfüllen, was den Compliance-Prozess vereinfacht.
Der Einsatz von Tools oder Plattformen, die automatisierte Cross-Mapping-Funktionen und umsetzbare Anleitungen bieten, kann diesen Prozess noch reibungsloser gestalten. Diese Ressourcen können Unternehmen dabei helfen, Audits zu optimieren, den Dokumentationsaufwand zu reduzieren und NIST CSF als universelles Framework zur Koordinierung der Compliance-Bemühungen über verschiedene Standards hinweg zu nutzen.
Was sind die Vorteile der Verwendung von Tools wie ISMS Copilot für das Compliance-Mapping?
Automatisierte Tools wie ISMS Copilot verändern die Art und Weise, wie Unternehmen Compliance-Mapping handhaben, und reduzieren den Zeit- und Arbeitsaufwand für die Abstimmung von Kontrollen über mehrere Frameworks hinweg erheblich. Aufgaben, die früher Wochen oder sogar Monate in Anspruch nahmen, können dank KI-gesteuerter Workflows nun in nur wenigen Tagen erledigt werden. Durch die Zentralisierung von Richtlinien, Nachweisen und Kontrolldefinitionen kann ISMS Copilot die Vorbereitungszeit für Audits um beeindruckende 75 bis 90 % reduzieren und gleichzeitig repetitive, zeitaufwändige Aufgaben eliminieren.
Die KI-Funktionen der Plattform gehen noch einen Schritt weiter, indem sie Lücken und Redundanzen minimieren. Sie empfiehlt sofort relevante Kontrollen für Frameworks wie NIST 800-53, ISO 27001 und SOC 2, wodurch Audits reibungsloser ablaufen und Ihre Sicherheitsmaßnahmen gestärkt werden. Darüber hinaus helfen Echtzeitüberwachung und KI-generierte Vorlagen den Teams, Risiken vorzubeugen, Fehler zu reduzieren und Kosten effektiver zu verwalten – für schnellere und zuverlässigere Compliance-Ergebnisse.
Wie können Unternehmen die Compliance über mehrere Sicherheitsframeworks hinweg aufrechterhalten?
Organisationen, die die Anforderungen mehrerer Compliance-Rahmenwerke erfüllen möchten, sollten die Erstellung eines einheitlichen Kontrollsatzes in Betracht ziehen. Dieser Ansatz hilft dabei, sich überschneidende Anforderungen aus Standards wie NIST CSF, ISO 27001, SOC 2 und NIST 800-53 aufeinander abzustimmen. Das NIST Cybersecurity Framework (CSF) bietet eine praktische Struktur – Identifizieren, Schützen, Erkennen, Reagieren, Wiederherstellen –, die als solide Grundlage für die Zuordnung dieser Rahmenwerke dienen kann.
Tools wie ISMS Copilot können Compliance-Maßnahmen optimieren, indem sie wichtige Aufgaben wie Kontrollzuordnung, Beweissammlung und Lückenanalyse automatisieren. Dieser KI-gestützte Assistent vereinfacht den Prozess, indem er maßgeschneiderte Richtlinien, Risikobehandlungspläne und Audit-Dokumentationen erstellt. Er passt sich außerdem an sich ändernde Vorschriften an und sorgt so für eine lückenlose Compliance. Mit Funktionen wie Echtzeitüberwachung und automatisierten Warnmeldungen können Teams potenzielle Probleme umgehend beheben und das ganze Jahr über für Audits gerüstet sein.

